As soon as your computer is connected to a network, you have to start thinking about security – security of your files, information, etc.
A network allows a person who does to have physical access to your computer (they are not sitting in front of it) to gain access all the same. If your computer is connected to a network, other people can connect to your computer.
A person who gains unauthorised access to a computer system is often called a hacker.
A network allows a person who does to have physical access to your computer (they are not sitting in front of it) to gain access all the same. If your computer is connected to a network, other people can connect to your computer.
A person who gains unauthorised access to a computer system is often called a hacker.

Preventing Unauthorised Access
There are a number of security measures that you can take to prevent hackers accessing your computer and all of the data stored on it:
Physical Security
The first thing to make sure of is that no unauthorised people can physically access (sit down in front of) any of the computers on your network.
For example, by keeping office doors locked.
For example, by keeping office doors locked.
Use a Username and Have a Good Password
The most common way to protect your computer’s data is to setup user accounts with usernames and passwords. Anyone not having a username, or not knowing the correct password will be denied access.
For this to be effective passwords must be chosen that are not easy to guess. Passwords should be a random combination of lowercase letters, uppercase letters and numbers (and symbols if this is allowed):
For this to be effective passwords must be chosen that are not easy to guess. Passwords should be a random combination of lowercase letters, uppercase letters and numbers (and symbols if this is allowed):
- ‘Weak’ passwords: password, 123456, david, 27dec1992
- ‘Strong’ passwords: s63gRdd1, G66ew$dQ, gdr298783X
Strong passwords are often hard to remember. Here is a good method for creating a password that is very strong, but also easy to remember:
Think of a phrase that you will never forget…
Think of a phrase that you will never forget…
“My favourite food is chocolate ice cream”
Take the first letter of each word…
mfficic
Change some letters to similar numbers: I to 1, o to 0, s to 5, etc. and make some letters (e.g. the first and last) uppercase…
Mff1c1C
A random-looking mixture of letters and numbers. As long as you like chocolate ice cream you will never forget your password!
Always Install and Use a Firewall
A firewall is a device, or a piece of software that is placed between your computer / LAN and the rest of the network / WAN (where the hackers are!)
You can read about firewalls in the Networking Hardware section.
You can read about firewalls in the Networking Hardware section.
Securing Your Data
Often we have data that is private or confidential. This data needs to be protected from being viewed by unauthorised people. This is especially true if the data is to be sent via a public network such as The Internet.
The best way to protect data is to encrypt it...
The best way to protect data is to encrypt it...
Data Encryption
Encryption is the process of converting information into a form that is meaningless to anyone except holders of a ‘key’.
For example, if Alice wants to send important, personal messages to Bob, she must go through the following steps...
For example, if Alice wants to send important, personal messages to Bob, she must go through the following steps...
Encryption has been used for centuries to protect secrets.
Military leaders as far back as roman times have used encryption to protect important messages sent to their armies, messages that must be kept secret from the enemy.
If the messenger was caught by the enemy, the message, being encrypted, remained secret because they didn’t know the code to decrypt it.
Military leaders as far back as roman times have used encryption to protect important messages sent to their armies, messages that must be kept secret from the enemy.
If the messenger was caught by the enemy, the message, being encrypted, remained secret because they didn’t know the code to decrypt it.
First Alice needs to generate a secret ‘key’.
The key is usually a very long, random number.
The key is usually a very long, random number.

The encryption scheme shown here is called Symmetric Key, or Single Key encryption.
There are many better schemes, such as Public Key Encryption, but the one shown here is the easiest to understand!
There are many better schemes, such as Public Key Encryption, but the one shown here is the easiest to understand!
Alice must then give a copy of this key to Bob. She must make sure that nobody else can get to the key
(So maybe Alice will visit Bob and give him a copy of the key on a memory stick or floppy disc).
(So maybe Alice will visit Bob and give him a copy of the key on a memory stick or floppy disc).
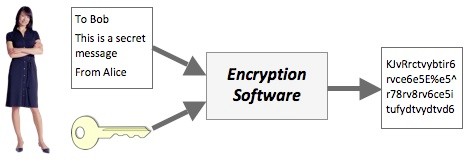
Now that Bob has a copy of the key, each time Alice needs to send him a message she starts by encrypting it using special encryption software and the secret key.
The encrypted message now looks like a jumble of random letters and numbers.
The encrypted message now looks like a jumble of random letters and numbers.
Alice then sends the encrypted message to Bob.
She can use a public network like the Internet, since, even if it gets stolen, the encrypted message cannot be read or understood without the key.
She can use a public network like the Internet, since, even if it gets stolen, the encrypted message cannot be read or understood without the key.

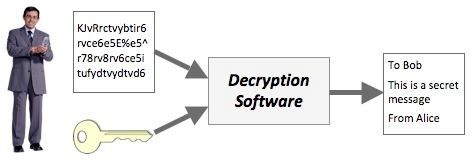
When Bob receives the message, he uses special decryption software and his copy of the secret key to decrypt the message.
Bob can now read the original message from Alice.
Bob can now read the original message from Alice.